A few weeks ago, the White House Office of Management and Budget (OMB) released a draft memorandum with the goals of enhancing the Federal Risk and Authorization Management Program, widely known as FedRAMP. In this blog post, we will go through a brief background on FedRAMP, then dive into the details of the OMB memo, and what it means for the future of FedRAMP. If you are familiar with FedRAMP, feel free to skip the background section.
Background on FedRAMP
FedRAMP is a program that allows the federal government to partner with agencies and third-party assessor organizations (3PAOs) to evaluate cloud service providers (CSPs) against a standard baseline of controls, namely NIST 800-53, and ultimately make risk-based decisions about adopting cloud-based products and services. Prior to FedRAMP, each government agency had their own process, making cloud adoption difficult and redundant.
Going through FedRAMP’s process means ultimately achieving an Authority to Operate (ATO) – a process that requires authoring a systems security plan (SSP), and going through an assessment from a 3PAO. Once a CSP achieves an ATO, they retrieve an authorized status in the FedRAMP Marketplace. This process is traditionally rigorous, taking months and sometimes even years. The graphic below outlines the process.
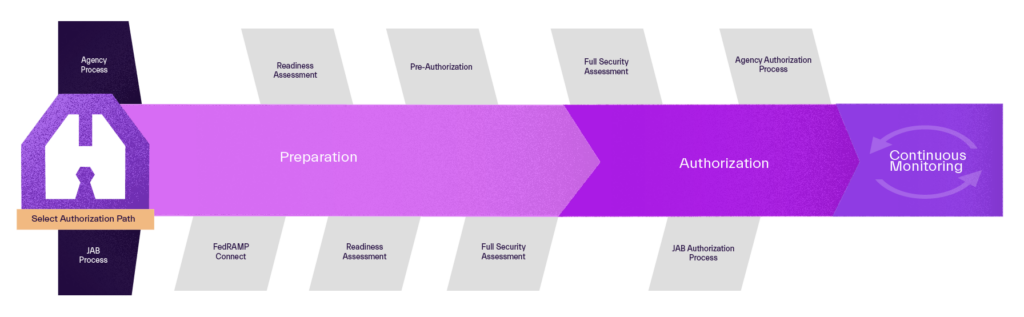
FedRAMP became codified in law earlier this year when President Joe Biden signed the FedRAMP Authorization Act as part of the National Defense Authorization Act (NDAA) for FY23. This means that if you offer a service, platform, or software that utilizes the cloud, and you want to sell to the federal government, you must go through FedRAMP’s process. This is a welcomed step in creating a standardized, reusable process for the federal government’s adoption of cloud-based technologies.
In addition, FedRAMP has become increasingly popular over recent years. According to fedramp.gov, FedRAMP authorized cloud products were reused more than 4500 times across the federal government, which represents a 60% increase in reuse from FY21 and a 132% increase from FY20. The FedRAMP community includes 204 participating agencies, 280+ cloud service providers (CSPs), and 40 recognized 3PAOs.
With the increased popularity of FedRAMP, and the involved process that it takes in order to achieve an ATO, the new FedRAMP OMB memo is a welcomed refresh of the program that will make the FedRAMP program more effective, for both commercial enterprises and government agencies. The memo’s aim is to increase Federal agencies’ adoption of cloud technologies while reducing risk and continuing to toil away redundant efforts.
Government Collaboration with the Industry
The significance of the recent memo is that it proposes guidance that would replace previous guidance that established the FedRAMP program more than a decade ago. This memo paves the way for a streamlined, scalable process that federal government agencies can follow to consume cloud services, and allows service providers an accelerated process to do business with the federal government.
Since its inception, FedRAMP has been a collaboration between the commercial sector and the government sector. This shared fate is inherent when the federal government consumes commercially available cloud services. A common theme throughout the recent OMB memo is the importance of this collaboration in order to stay on top of the latest threats while implementing the latest and greatest security measures.
From IaaS to SaaS
When FedRAMP was first introduced, the federal government was primarily focused on enabling cloud services providers that provide Infrastructure as a Service (IaaS) to do business with the federal government. Examples of IaaS include Amazon Web Services, Google Cloud, and Microsoft Azure. In recent years, the cloud service provider landscape has changed, and shifted towards software as a service (SaaS), with tools such as Salesforce, Slack, or GitHub being examples. With SaaS, cloud service providers are responsible for securing their software and customer data – rather than having to secure the infrastructure, allowing for a quicker go to market and easier collaboration. IaaS and SaaS have different security concerns due to the shared responsibility of the cloud provider versus the customer, as shown in the graphic below.
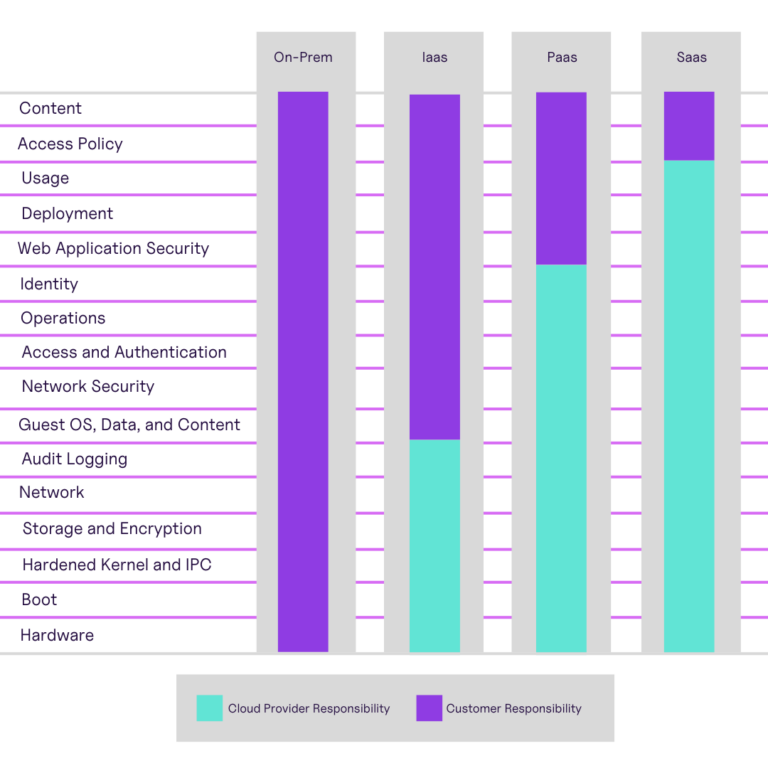
The usage of commercially available SaaS products allows an organization to free up resources that would typically be used as in-house personnel that would have to tend to infrastructure. This allows for greater dedication to product development – or for a government agency, mission operations. In the OMB memo, the realization that a federal agency may only rely on a few IaaS providers, but can rely on hundreds of SaaS providers is outlined, and as such FedRAMP should adjust to further take advantage of commercially available cloud services.
GovClouds
FedRAMP has enabled the federal government to adopt cloud services at a greater speed, and as such CSPs have been innovating to cater to government workloads – a great example of this is the AWS GovCloud. The OMB memo calls this out, explicitly stating that FedRAMP should not incentivize commercial CSPs to create dedicated infrastructure for federal government use, but instead incorporate these security measures into their typical infrastructure. A good example of IaaS incorporating security measures into their infrastructure is Google Cloud, which doesn’t have a specific GovCloud-type offering (mind the service-by-service caveats and Assured Workloads as to whether or not they are FedRAMP authorized). Although the examples above are calling out primarily IaaS/PaaS providers, this advice is equally applicable for federal-specific SaaS offerings.
Within a year of the issuance of the OMB memo (most likely before 2025), GSA will create a roadmap to structure FedRAMP and encourage the transition away from the use of cloud infrastructure created specifically for the federal government.
Scaling the FedRAMP Marketplace
Although FedRAMP has created a unified process for the government to adopt cloud services, it has fallen short of the scalability needed in a market of tens of thousands of solutions. As of writing this blog, there are a total of 321 authorized services in the FedRAMP Marketplace. With the federal government’s increasing adoption of the cloud, in particular SaaS based services, the OMB has outlined that the marketplace must scale (well into the thousands) in order to keep up with the demand of the federal government. Adoption of SaaS is critical in reducing the IT footprint of federal agencies, and thus inherently increasing security through a public/commercial collaboration.
In order to scale the FedRAMP marketplace, the memo suggests offering multiple authorization structures. In addition, the memo encourages FedRAMP to provide assistance to small or disadvantaged businesses that may face challenges in accessing the marketplace.
FedRAMP Authorizations
Up to this point, there have been two authorization paths for an authorization: an authorization by a single sponsoring agency or an authorization by the joint authorization board (JAB). In order to facilitate efforts to accommodate different use cases within in the federal government, the OMB memo states that FedRAMP will support multiple types of authorizations:
Single-Agency Authorization: when a single federal agency has assessed a cloud service’s security posture and has found it acceptable.
Joint-Agency Authorization: when two or more federal agencies have assessed a cloud service’s security posture and have found it acceptable.
Program Authorization: when the FedRAMP program has assessed a cloud service’s posture and has found it acceptable for re-use by federal agencies.
Any other type of Authorization: authorizations that are designed by the FedRAMP PMO (Program Management Office) and approved by the FedRAMP Board to promote further goals of the FedRAMP program.
The fourth authorization path seems the most ambiguous (since it’s at the discretion of the FedRAMP PMO), and the third authorization path is a good addition to the single-agency and join-agency authorization paths.
Another important detail from the OMB memo is allowing a FedRAMP “preliminary authorization” that allows a cloud service to be trialed for up to 12 months, and will hopefully fast track the process of receiving a FedRAMP ATO. This provides an interesting on-ramp for smaller businesses or more novel technologies that could be beneficial to the federal government.
FedRAMP Automation
The OMB memo holds automation as an essential component of the future of FedRAMP. The memo mentions that “it is essential that FedRAMP establish an automated process for the intake of industry standard security assessments and reviews,” and mandates that the GSA establishes a way to automate FedRAMP security assessments and reviews by December 3rd, 2023. Automation in the FedRAMP process, just like other processes within the realm of cloud security, reduces the burden on IT, security, and compliance teams while increasing the speed of delivery of secure workloads. Furthermore, the OMB memo states that the “authorization process must integrate agile principles” – principles that are facilitated by the automation of process, the collaboration amongst people, and the implementation of the latest technologies.
The memo’s emphasis on automation and machine-readable data encourages cloud service providers to provide self-service capabilities through APIs and interoperable standards to collect any artifacts that are relevant to FedRAMP authorization. Within 18 months (most likely in 2025) GSA will receive the artifacts mentioned above exclusively through automated methods.

HanaByte is leading the pack when it comes to this type of FedRAMP automation. When assisting our customers with their compliance automation, we create SSPs using interoperable standards such as the open security controls assessment language (OSCAL). OSCAL was created by NIST, in collaboration with the industry, and allows for authoring and submitting SSPs in a machine readable format, exactly what the memo is referring to. Embracing this type of approach is central to our goal of blurring the lines between compliance and automation – enabling DevOps and platform teams to collaborate effectively with GRC and security teams. For more information on OSCAL, check out our blog that gives an introduction to it.
Inter-Agency FedRAMP Acceleration
Encouraging the use of security and compliance tooling, which allows easy yet automated FedRAMP ingestion of security control evidence and continuous monitoring information, paves the way for accelerated ATOs throughout the federal government. These artifacts can be shared (and are encouraged by this memo to do so) to provide additional agency ATOs.
FedRAMP and Other Compliance Frameworks
The OMB memo identifies that the current process of performing assessments of additional frameworks each time a product that goes through the FedRAMP process slows down federal government adoption of the software. In order to remove this slowdown, FedRAMP will find a way to leverage these existing frameworks as part of the risk assessment for agencies. Examples of this include using control assessments from external parties instead of performing new ones during a FedRAMP ATO process.
Even more interesting is that, for lower risk cloud services, there could be certifications that can be provided instead of a full FedRAMP authorization. FedRAMP would have to reconcile any gaps or misalignments between external frameworks and those used in the federal government.
HanaByte helps cloud service providers reach their goals with a variety of existing frameworks that may be leveraged in the future to assist with FedRAMP authorizations per this guidance. HanaByte assists organizations with well known industry standards such as PCI DSS, SOC 2, ISO 27k, and HITRUST.
Continuous Monitoring
Continuous Monitoring has always been a part of the FedRAMP ATO process, as agencies require evidence of continuous monitoring activities on a consistent, periodic basis. The OMB memo encourages FedRAMP to develop processes that don’t disrupt agility from a cloud service provider perspective, wherever possible.
The memo mentions a framework that encourages: automation and DevSecOps best practices, allowing FedRAMP authorized cloud services to innovate and make security changes without prior approval from the government, coordinate with the Cybersecurity and Infrastructure Security Agency (CISA) with technical data to detect threats and risks from the cloud, discouraging government-specific distributions of cloud services, and give cloud providers clear expectations for incident response activities. In addition, the FedRAMP PMO will perform its own continuous monitoring of the cloud service providers based on the level of security impact of particular security controls. When the FedRAMP PMO finds a vulnerability with a cloud service provider that has an ATO, the PMO will coordinate with CISA, OMB, and the FedRAMP board for responding to incidents. Continuous Monitoring changes congruent with this memo will be implemented late 2023, or sometime in 2024 (specifically within 180 days of the issuance of the memo).
HanaByte specializes in deploying landing zones, powered by Infrastructure as Code that meets the continuous monitoring requirements of FedRAMP and adhere to NIST 800-53 baseline controls. For an article that outlines one of the landing zone approaches we take on AWS, check out this article.
The FedRAMP Board
The memo establishes a FedRAMP Board that consists of “up to seven senior officials or experts from agencies that are appointed by OMB in consultation with GSA.” These board members provide oversight, input, recommendations, and guidance for the FedRAMP program to ensure a successful FedRAMP program. This FedRAMP Board will be established late 2023, or sometime in 2024 (specifically within 90 days of the issuance of the memo).
Industry Engagement
The OMB memo iterates that FedRAMP is a bridge between the commercial and Federal community. In this respect, the FedRAMP PMO and Board will seek feedback from industry leaders through means such as the Federal Secure Cloud Advisory Committee (FSCAC) as appropriate. This private/public sector collaboration should create a feedback loop to achieve accelerated ATOs and provide innovative cloud services to the federal government.
Looking Forward
There are many changes coming to the FedRAMP program, and if you are running a cloud service that may need authorization in the future, it’s important to keep these changes in mind. HanaByte was founded by dog lovers and DevSecOps practitioners who focus on blurring the lines between compliance and automation. We are well equipped to help organizations of all sizes achieve their ATO at an accelerated rate per the guidance of the recent OMB memo and the upcoming changes to FedRAMP. Let’s embark on your security journey today!









